3. Sensitive Data Exposure
[Severity 3] Sensitive Data Exposure (Introduction)
When a webapp accidentally divulges sensitive data, we refer to it as "Sensitive Data Exposure". This is often data directly linked to customers (e.g. names, dates-of-birth, financial information, etc), but could also be more technical information, such as usernames and passwords. At more complex levels this often involves techniques such as a "Man in The Middle Attack", whereby the attacker would force user connections through a device which they control, then take advantage of weak encryption on any transmitted data to gain access to the intercepted information (if the data is even encrypted in the first place...). Of course, many examples are much simpler, and vulnerabilities can be found in web apps which can be exploited without any advanced networking knowledge. Indeed, in some cases, the sensitive data can be found directly on the webserver itself...
The web application in this box contains one such vulnerability. Deploy the machine, then read through the supporting material in the following tasks as the box boots up.
Answer the questions below
Read the introduction to Sensitive Data Exposure and deploy the machine
No answer needed
[Severity 3] Sensitive Data Exposure (Supporting Material 1)
The most common way to store a large amount of data in a format that is easily accessible from many locations at once is in a database. This is obviously perfect for something like a web application, as there may be many users interacting with the website at any one time. Database engines usually follow the Structured Query Language (SQL) syntax; however, alternative formats (such as NoSQL) are rising in popularity.
In a production environment it is common to see databases set up on dedicated servers, running a database service such as MySQL or MariaDB; however, databases can also be stored as files. These databases are referred to as "flat-file" databases, as they are stored as a single file on the computer. This is much easier than setting up a full database server, and so could potentially be seen in smaller web applications. Accessing a database server is outwith the scope of today's task, so let's focus instead on flat-file databases.
As mentioned previously, flat-file databases are stored as a file on the disk of a computer. Usually this would not be a problem for a webapp, but what happens if the database is stored underneath the root directory of the website (i.e. one of the files that a user connecting to the website is able to access)? Well, we can download it and query it on our own machine, with full access to everything in the database. Sensitive Data Exposure indeed!
That is a big hint for the challenge, so let's briefly cover some of the syntax we would use to query a flat-file database.
The most common (and simplest) format of flat-file database is an sqlite database. These can be interacted with in most programming languages, and have a dedicated client for querying them on the command line. This client is called "sqlite3", and is installed by default on Kali.
Let's suppose we have successfully managed to download a database:
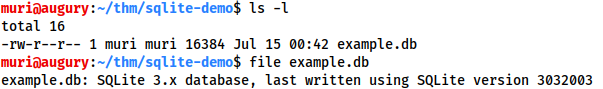
We can see that there is an SQlite database in the current folder.
To access it we use: sqlite3 <database-name>:
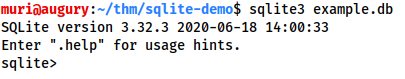
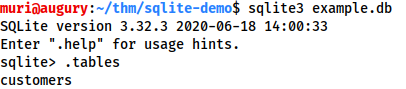
From here we can see the tables in the database by using the .tables command:
At this point we can dump all of the data from the table, but we won't necessarily know what each column means unless we look at the table information. First let's use PRAGMA table_info(customers); to see the table information, then we'll use SELECT * FROM customers; to dump the information from the table:
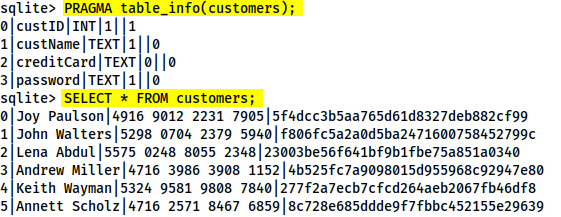
We can see from the table information that there are four columns: custID, custName, creditCard and password. You may notice that this matches up with the results. Take the first row:
0|Joy Paulson|4916 9012 2231 7905|5f4dcc3b5aa765d61d8327deb882cf99
We have the custID (0), the custName (Joy Paulson), the creditCard (4916 9012 2231 7905) and a password hash (5f4dcc3b5aa765d61d8327deb882cf99).
In the next task we'll look at cracking this hash.
Answer the questions below
Read and understand the supporting material on SQLite Databases.
No answer needed
[Severity 3] Sensitive Data Exposure (Supporting Material 2)
In the previous task we saw how to query an SQLite database for sensitive data. We found a collection of password hashes, one for each user. In this task we will briefly cover how to crack these.
When it comes to hash cracking, Kali comes pre-installed with various tools -- if you know how to use these then feel free to do so; however, they are outwith the scope of this material.
Instead we will be using the online tool: Crackstation. This website is extremely good at cracking weak password hashes. For more complicated hashes we would need more sophisticated tools; however, all of the crackable password hashes used in today's challenge are weak MD5 hashes, which Crackstation should handle very nicely indeed.
When we navigate to the website we are met with the following interface:
Let's try pasting in the password hash for Joy Paulson which we found in the previous task (5f4dcc3b5aa765d61d8327deb882cf99). We solve the Captcha, then click the "Crack Hashes" button:
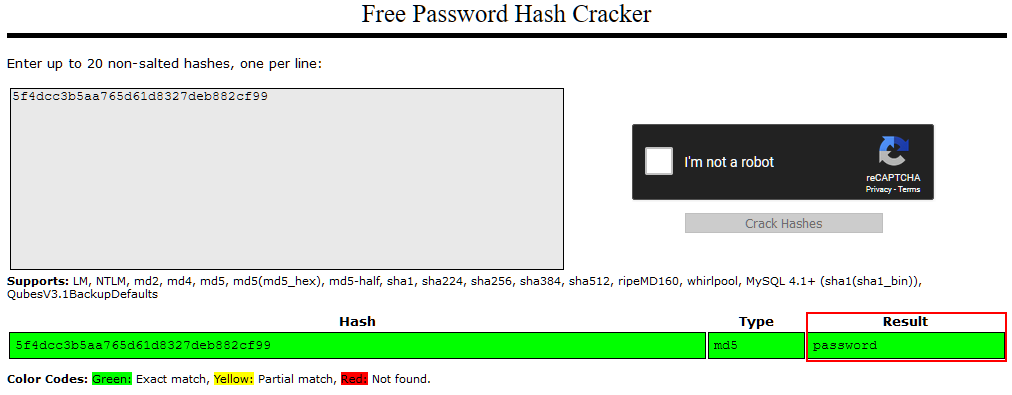
We see that the hash was successfully broken, and that the user's password was "password" -- how secure!
It's worth noting that Crackstation works using a massive wordlist. If the password is not in the wordlist then Crackstation will not be able to break the hash.
The challenge is guided, so if Crackstation fails to break a hash in today's box you can assume that the hash has been specifically designed to not be crackable.
Answer the questions below
Read the supporting material about cracking hashes.
No answer needed
[Severity 3] Sensitive Data Exposure (Challenge)
It's now time to put what you've learnt into practice!
Answer the questions below
Have a look around the webapp. The developer has left themselves a note indicating that there is sensitive data in a specific directory. What is the name of the mentioned directory?
nmap scan to verify web app port
directory busting
/assets
Navigate to the directory you found in question one. What file stands out as being likely to contain sensitive data?

webapp.db
Use the supporting material to access the sensitive data. What is the password hash of the admin user?
check database type after download
SQLite 3.x database
extract data
if these fields looks weird ... print columns name
password hash of the admin user : 6eea9b7ef19179a06954edd0f6c05ceb
Crack the hash. What is the admin's plaintext password?
lets use crackstation


admin's plaintext password : qwertyuiop
Login as the admin. What is the flag?
login using this credentials admin:qwertyuiop

THM{Yzc2YjdkMjE5N2VjMzNhOTE3NjdiMjdl}
Last updated